Why choose us
Check our professional services
In need of a professional SIEM Solution? Check the SIEM Soultions from CyStrat Solutions!
CyStrat SOC Suite SIEM
Our advanced SIEM Solution empowers organizations to proactively detect, investigate, and respond to cyber threats in real-time. With robust event correlation, intelligent analytics, and automated incident response capabilities, our SIEM solution ensures comprehensive protection for your critical assets. Stay one step ahead of attackers and strengthen your security posture with our industry-leading SIEM technology
CyStrat SOC Suite SOAR Solution
Supercharge your security operations with our SOAR solution which is fully integratible to the CyStrat SOC SIEM. Our comprehensive platform combines intelligent automation, seamless orchestration, and rapid response capabilities to revolutionize your incident management processes. From threat detection to automated incident triage and remediation, our SOAR solution empowers your security team to work smarter, respond faster, and stay one step ahead of cyber threats. Experience the power of streamlined security operations and elevate your organization's defense against evolving risks with our industry-leading SOAR technology.
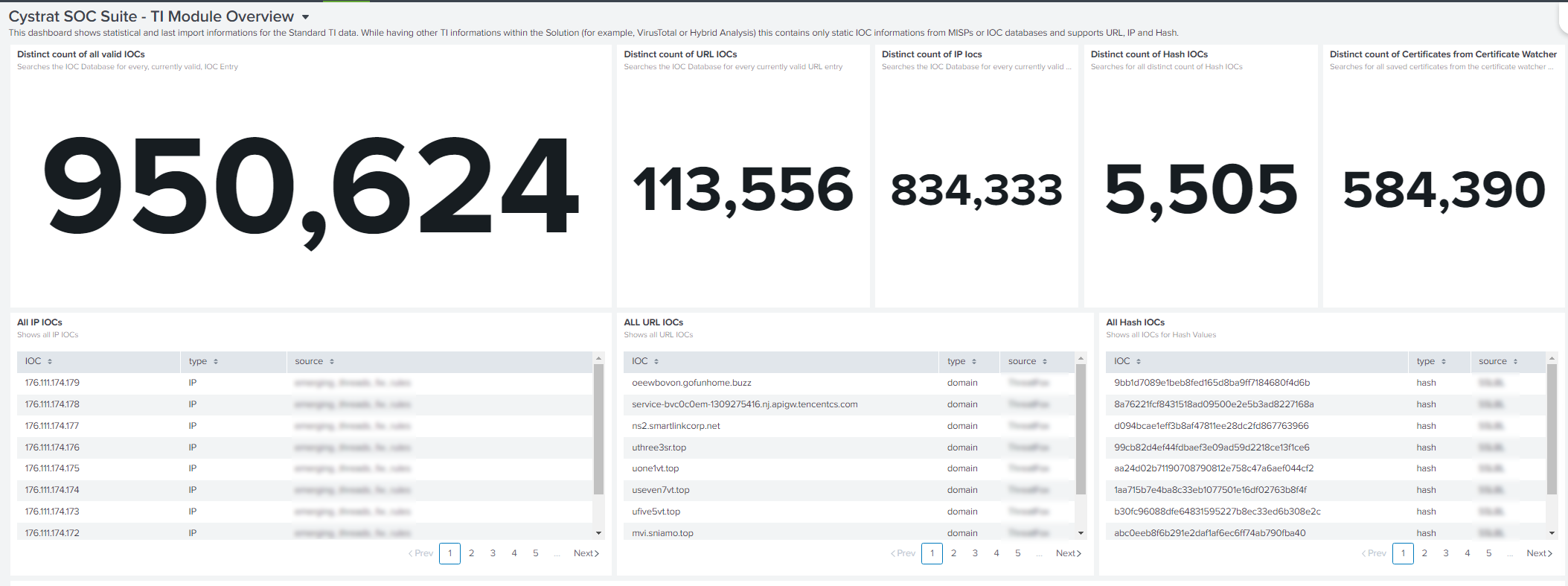
CyStrat SOC Suite Threat Intelligence
Introducing our revolutionary Threat Intelligence (TI) module with automated threat detection. Our solutions allows real-time monitoring to identify and mitigate a wide range of cyber threats. From malware and ransomware to zero-day exploits and advanced persistent threats, our TI module is another step to keep your organization protected against emerging risks.